This post will guide you how to use Kusto query to classify the log data based on some log is just contain a string, and you want to separate the string into different column for easy view.
For clearer, if you receive the syslog message like:
%ASA-3-710003: TCP access denied by ACL from 109.248.6.239/46449 to outside:172.16.1.211/80
You need to separate the above example syslog message with column “DeviceName”, “DeviceIP”, “SyslogID” and “SeverityLevel”.
However, you do not want to use the original data such as “SeverityLevel”, this example message show is “NOTI”, you do not want to use “NOTI” as the target “SeverityLevel”, you want to use like “notice” as final “SeverityLevel”, this post also will guide you how to make it.
The steps for the whole configuration will be:
- Create a new Workbook
- Develop a customized Workbook for Cisco Device
- Log Data Classification
Step 1 – Create a new Workbook
Visit to “Sentinel” and select “Workbook”, then click “Add workbook” to create a blank workbook.
Step 2 – Develop a customized Workbook for Cisco Device
For the Sentinel Workbook, you can make the dashboard like our example.
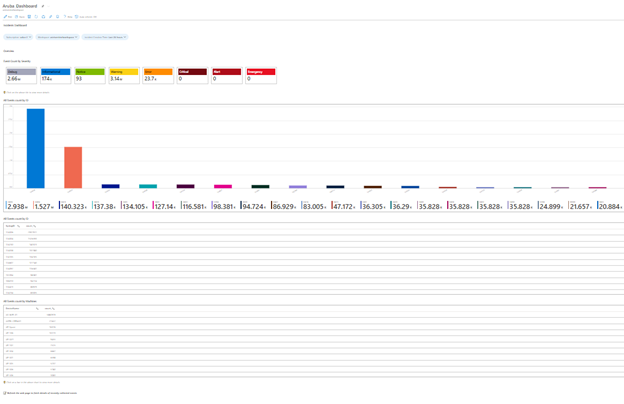
For Workbook Design detail information, please visit our post:
Azure Sentinel – A Guide for Customizing Sentinel Workbook (Kusto Query) for Sentinel Incidents
Step 3 – Log Data Classification
This is the primary KQL for the log data classification for Cisco Device Syslog Message:
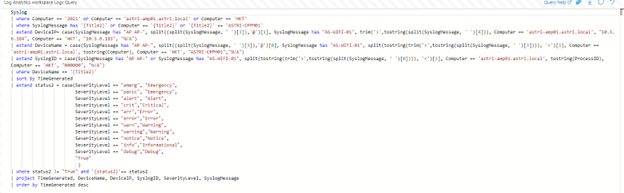
For the above example, you need to extend the custom column and use some string operation for doing the log data classification.
You can visit our SOS GitHub for downloading the source code as a template:
https://github.com/SOSHKMVP/AzureSentinel-Workbook/blob/main/Cisco_Dashboard.txt

Eric Chan
Microsoft MVP
SOS Group Limited

